This project uses Terraform, a very powerful Infrastructure as Code(IaC) tool to deploy a two-tier Architecture on AWS that contains an Application Load Balancer, Auto Scaling Group, Route53 domain name, etc.
This project is a redo of my past projects where I created the same Infrastructure using the AWS console instead. Here's the link to the old project: https://blog.ajim.me/hosting-a-highly-available-fault-tolerant-website-on-aws.
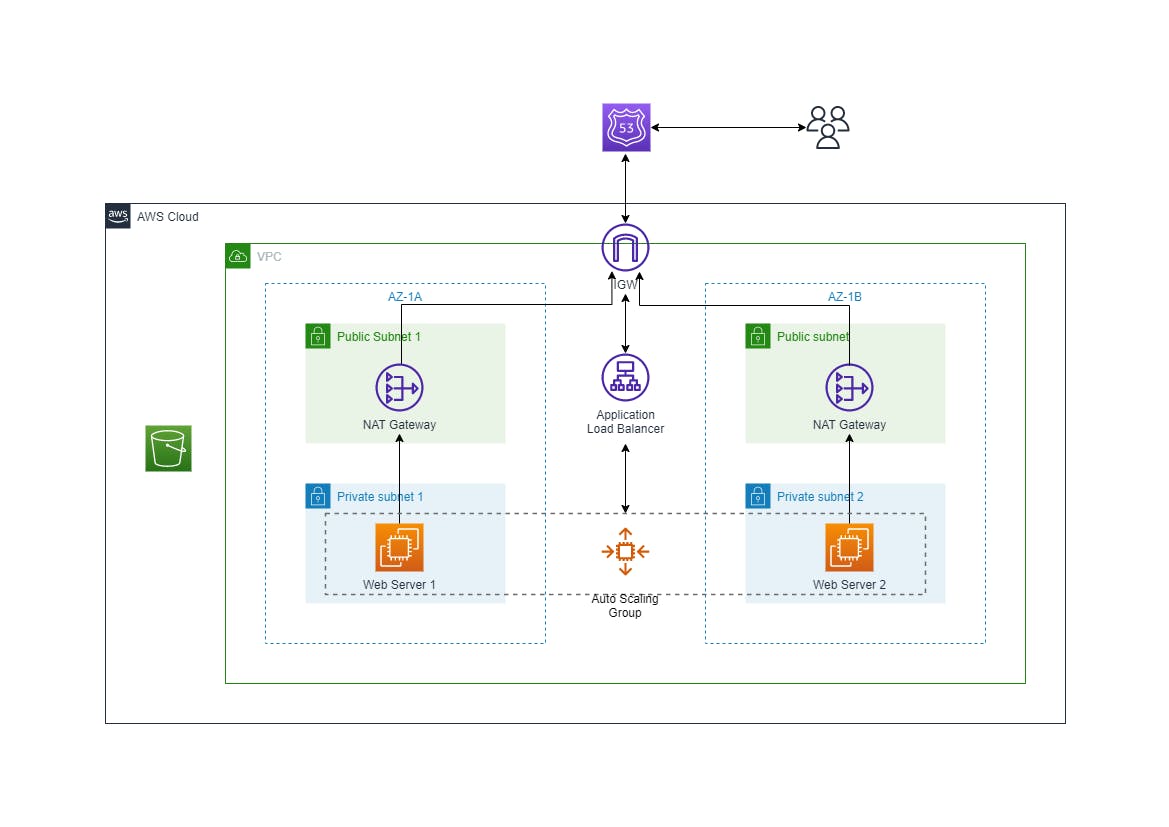
The image below is the reference Architecture Diagram that was used.
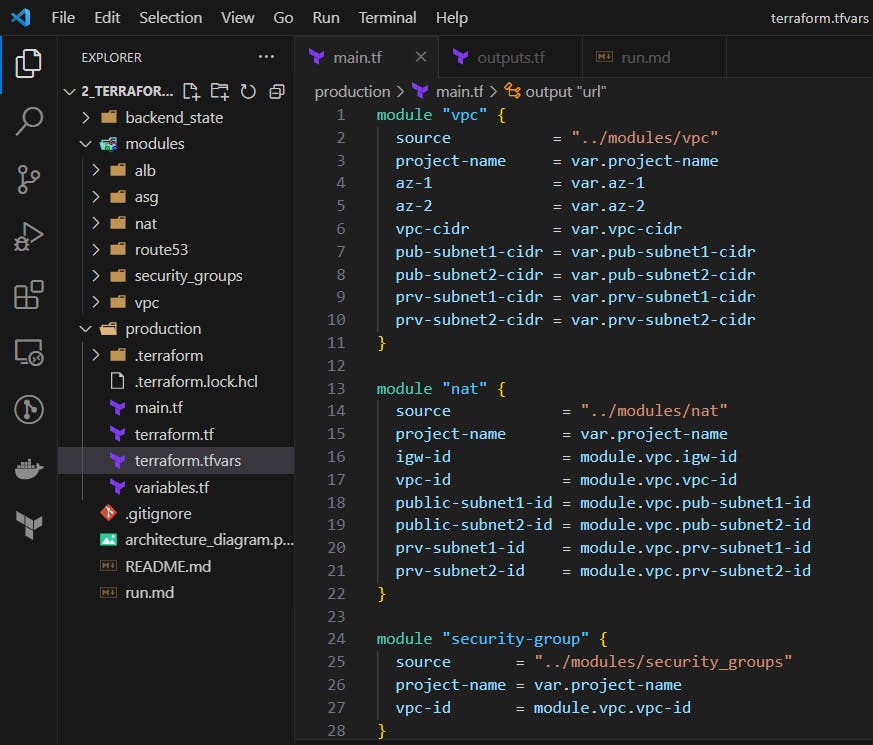
The code structure
You can access the source code here on my GitHub: https://github.com/ajimbong/terraform-modules-project.
But I'll walk you through the structure of the project and what makes up the different components:
Backend State
From the image above, the first folder we have is 📁backend_state which stores the terraform code that creates the remote S3 and DynamoDB table that we will later use to store the state file for our project. So if you want to run this project, you will need to first run the code in that directory to provision those resources; unless you will use the local backend instead.
Modules
The 📁modules folder contains all the modules for this project in the various sub-folders.
1) alb
📁alb is the module that is responsible for creating the Application Load Balancer. Like all other modules, it has attributes that have to be provided at the time of creating the module and some attributes depend on the output of other modules.
2) asg
📁asg is the Auto Scaling Group Module and it contains the Launch Configuration which will be used by the ASG to create EC2 instances. It also has an IAM role to access AWS S3 service which is used to pull down the web files from a defined bucket when launching the EC2 instances; These web files are placed in a directory for the Apache web server to serve.
3) nat
📁nat module will create two NAT gateways in the public subnet with elastic IP addresses. This module also creates two private route tables that belong to their respective availability zones.
4) route53
📁rout53 module pulls down an existing hosted zone using the data block and creates a record that will be attached to the Application Load Balancer. This module is not too essential and can be left out if you haven't bought a domain name with route53.
5) security_groups
📁security_groups module creates two security groups, one for the Application Location Balancer and the other which is used by the EC2 servers.
6) vpc
📁vpc modules creates the underlying network stack for the architecture with 2 public subnets, 2 private subnets, 1 internet gateway, and a route table that is used by all the public subnets.
Production
The 📁production folder is basically where we put it all together and import all the modules to create this architecture. terraform.tfvars is the file we use to pass in the variables needed by all these modules. Note that we can create multiple instances of this architecture probably for Staging, Testing etc just by importing the modules and passing the required arguments.

